Warning: The configuration is only an example, even though you can use the exact configuration and your FreeRADIUS Server will work as intended for this guide, you should still make sure only allowed devices can use the FreeRADIUS Server and only allowed authentication protocols are specified. Some options can be removed, but are left here for debugging purposes. I was asked in because Mikrotik specialists in Cape Town are hard to find, and harder to schedule. I looked around for solutions to his problem, and decided on a Freeradius installation on Ubuntu, backed up with a mysql database and Freeradius-dialupadmin as a web front end for management. 7 thoughts on “ CARA KONFIGURASI MIKROTIK + FREERADIUS (linux) + MYSQL (linux) ” pepep says: February 19, 2015 at 9:36 am Wih postingan yang keren, dan belum saya temukan di blog lain selain selama 5-6 bulan terakhir. Baru ini yang langkah2nya sangat lengkap dan terperinci. MikroTik Radius Configuration with FreeRADIUS and MySQL December 18, 2018 Abu Sayeed FreeRADIUS Server, Linux Server Configuration, MikroTik Router, RADIUS Server, Red Hat/CentOS Linux FreeRADIUS is a modular RADIUS suite. A lot of modules such as Perl, python, MySQL etc. Can be integrated with freeRADIUS to enrich freeRADIUS features.
Applies to RouterOS: v6.41 +

- 2Configuration

Password-less (certificate based or private/public key based) authentication is great for security, though setting up is not always straight forward. This guide will show you how to set up WPA/WPA2 EAP-TLS authentication using RouterOS and FreeRADIUS. In this example we are going to use Debian and FreeRADIUS to process RADIUS requests, RouterOS as a RADIUS Client, RouterOS to generate required server/client certificates and RouterOS as a Wireless Client to connect to a WPA/WPA2 EAP-TLS secured network.
In this guide we are going to assume the following:
- 10.0.0.1 - our main gateway/Router-CA (going to be used to generate certificates, can be the same device as the Wireless AP)
- 10.0.0.2 - our FreeRADIUS Server
- 10.0.0.3 - our Wireless AP
Router-CA
In this example we are going to use a RouterOS device to generate required certificates, it is not required, but RouterOS is very convenient to generate certificates, use these commands on your Router-CA (this can be done on any RouterOS device, does not even need to be connected to the same network):
Note: Be sure to set the correct common-name for the FreeRADIUS Client device, this must match the supplicant-identity.
Freeradius Install
Download the following files and upload them to the appropriate destination:
- cert_export_FreeRADIUS_Server.crt -> FreeRADIUS Server: /etc/ssl/FreeRADIUS/
- cert_export_FreeRADIUS_Server.key -> FreeRADIUS Server: /etc/ssl/FreeRADIUS/
- cert_export_LocalCA.crt -> FreeRADIUS Server: /etc/ssl/FreeRADIUS/
- cert_export_LocalCA.crt -> Wireless Client: /
- cert_export_FreeRADIUS_Client.crt -> Wireless Client: /
- cert_export_FreeRADIUS_Client.key -> Wireless Client: /
Note: To download these certificates you can use Winbox (File section) or you can use a FTP Client to download them, they should appear in the root directory of the device when you connect to it. You can also use Fetch Tool to upload them to a remote location, there are other ways to get files out of your devices, the methods mentioned are only the most common ones.

FreeRADIUS Server
Here we are assuming you have already set up FreeRADIUS Server on your Debian box, below you can find the configuration file for /etc/freeradius/3.0/sites-enabled/default:
Note: By default the inner-tunnel site is enabled, you might want to disable it since it can cause security issues.
Configuration for /etc/freeradius/3.0/mods-enabled/eap:
Create the temporary directory for certificate verification and set proper permissions on it:
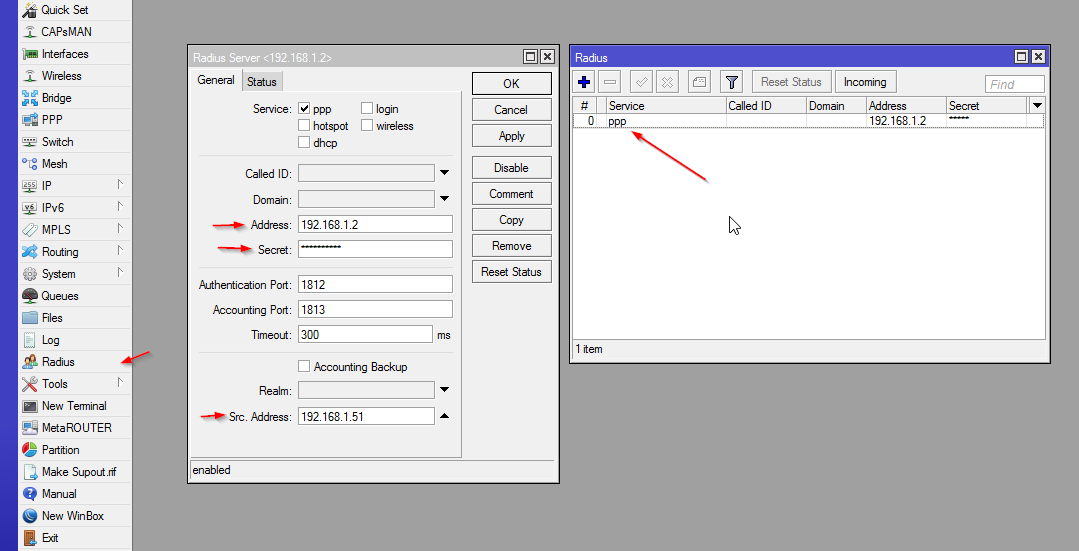
Don't forget to allow connections from our RAIDUS Client in /etc/freeradius/3.0/clients.conf:
Restart the service:
Warning: The configuration is only an example, even though you can use the exact configuration and your FreeRADIUS Server will work as intended for this guide, you should still make sure only allowed devices can use the FreeRADIUS Server and only allowed authentication protocols are specified. Some options can be removed, but are left here for debugging purposes. Some options match with the default values.
Wireless AP
Configure the RADIUS Client:
Setup the Wireless interface to use WPA2 EAP-TLS:
Freeradius Mysql Mikrotik Hotspot
Note: When the AP is used for passthrough it is not required to add certificates on the AP itself, the AP device works as a transparent bridge and forwards the EAP-TLS association data from RADIUS server to the end client.
Wireless Client
Freeradius Mysql Mikrotik App
Import the certificate files:
Freeradius Mysql Mikrotik Tutorial
Setup up the Wireless interface:
Note: Make sure the supplicant-identity matches the common-name when generated the certificate.
The Wireless Client should now be authenticated. That is it!

